Google on Tuesday said it's piloting a new feature in Chrome called Device Bound Session Credentials (DBSC) to help protect users against session cookie theft by malware.
The prototype – currently tested against "some" Google Account users running Chrome Beta – is built with an aim to make it an open web standard, the tech giant's Chromium team said.
"By binding authentication sessions to the device, DBSC aims to disrupt the cookie theft industry since exfiltrating these cookies will no longer have any value," the company noted.
"We think this will substantially reduce the success rate of cookie theft malware. Attackers would be forced to act locally on the device, which makes on-device detection and cleanup more effective, both for anti-virus software as well as for enterprise managed devices."
The development comes on the back of reports that off-the-shelf information stealing malware are finding ways to steal cookies in a manner that allows threat actors to bypass multi-factor authentication (MFA) protection and gain unauthorized access to online accounts.
Such session hijacking techniques have been around for years. In October 2021, Google's Threat Analysis Group (TAG) detailed a phishing campaign that targeted YouTube content creators with cookie stealing malware to hijack their accounts and monetize the access for perpetrating cryptocurrency scams.
Earlier this January, CloudSEK revealed that information stealers like Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and WhiteSnake have updated their capabilities to hijack user sessions and allow continuous access to Google services even after a password reset.
Google told The Hacker News at the time that "attacks involving malware that steal cookies and tokens are not new; we routinely upgrade our defenses against such techniques and to secure users who fall victim to malware."
It further recommended users to enable Enhanced Safe Browsing in the Chrome web browser to protect against phishing and malware downloads.
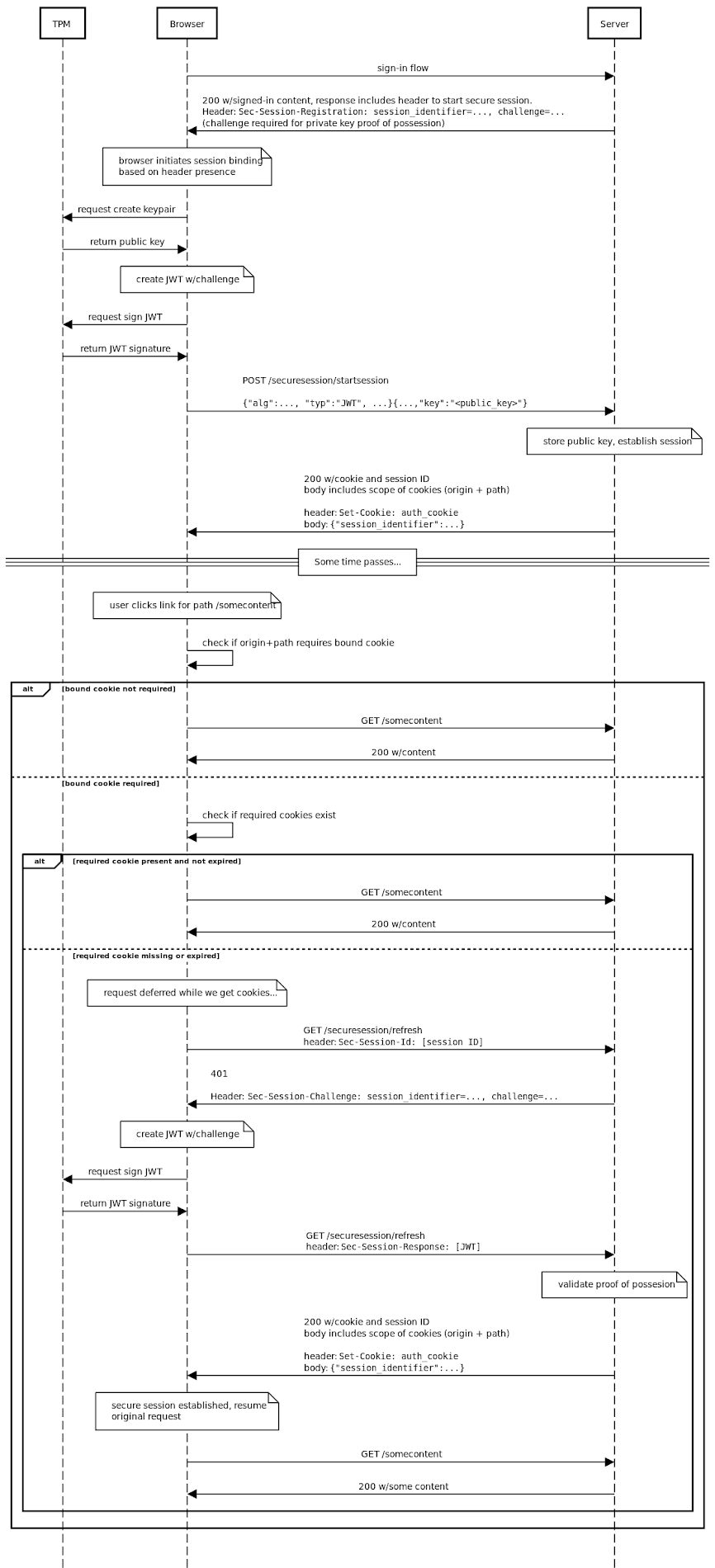
DBSC aims to cut down on such malicious efforts by introducing a cryptographic approach that ties together the sessions to the device such that it makes it harder for the adversaries to abuse the stolen cookies and hijack the accounts.
Offered via an API, the new feature achieves this by allowing a server to associate a session with a public key created by the browser as part of a public/private key pair when a new session is launched.
It's worth noting that the key pair is stored locally on the device using Trusted Platform Modules (TPMs). In addition, the DBSCI API permits the server to verify proof-of-possession of the private key throughout the session lifetime to ensure the session is active on the same device.
"DBSC offers an API for websites to control the lifetime of such keys, behind the abstraction of a session, and a protocol for periodically and automatically proving possession of those keys to the website's servers," Google's Kristian Monsen and Arnar Birgisson said.
"There is a separate key for each session, and it should not be possible to detect that two different session keys are from one device. By device-binding the private key and with appropriate intervals of the proofs, the browser can limit malware's ability to offload its abuse off of the user's device, significantly increasing the chance that either the browser or server can detect and mitigate cookie theft."
One crucial caveat is that DBSC banks on user devices having a secure way of signing challenges while protecting private keys from exfiltration by malware, necessitating that the web browser has access to the TPM.
Google said support for DBSC will be initially rolled out to roughly half of Chrome's desktop users based on the hardware capabilities of their machines. The latest project is also expected to be in sync with the company's broader plans to sunset third-party cookies in the browser by the end of the year via the Privacy Sandbox initiative.
"This is to make sure that DBSC does not become a new tracking vector once third-party cookies are phased out, while also ensuring that such cookies can be fully protected in the meantime," it said. "If the user completely opts out of cookies, third-party cookies, or cookies for a specific site, this will disable DBSC in those scenarios as well."
The company further noted that it's engaging with several server providers, identity providers (IdPs), and browser vendors like Microsoft Edge and Okta, who have expressed interest in DBSC. Origin trials for DBSC for all supported websites are set to commence by the end of the year.